Introduction
My research group develops methods to secure computing systems by
understanding attacks, developing defenses, and devising metrics
by which we can show that our defenses work. Some projects require
expertise in program analysis and transformation, some projects utilize
expertise in operating systems, and some projects include elements of
both.
In collaboration with
Robert Walls at
Worcester Polytechnic Institute (WPI),
we have devised new methods of hardening software running on
micro-controllers: small embedded systems that often impose real-time
constraints on software. We first developed a write-protected
shadow stack for these micro-controllers that is, to the best of our
knowledge, the fastest write-protected shadow stack for ARM processors
today. We then extended this work to provide holistic control flow
integrity for an entire embedded system (including its real-time
operating system).
In parallel, we have developed alternative methods of mitigating
control-flow hijacking attacks against embedded systems. We developed
an efficient method of enforcing execute-only memory (XOM) using the
debugging features of modern ARM processors, and we have used it in a
novel randomization system called Randezous which makes
randomization measurably effective for such resource-limited
microcontrollers.
Papers
Shade and Ombro
Over the past several years, we have enhanced
Secure Virtual Architecture (SVA) with support for hypervisor code.
We first extended Virtual Ghost and Apparition to support hypervisor
code; we dub this system Shade. Like its predecessors, Shade
protects applications from an untrusted operating system kernel.
More recently, we ported the Xen hypervisor to SVA and added features
provide a write-protected shadow stack. This system,
named Ombro, defeats advanced control-flow hijacking attacks
against hypervisors, thereby preventing virtual machine escape attacks.
Papers
Virtual Ghost and Apparition
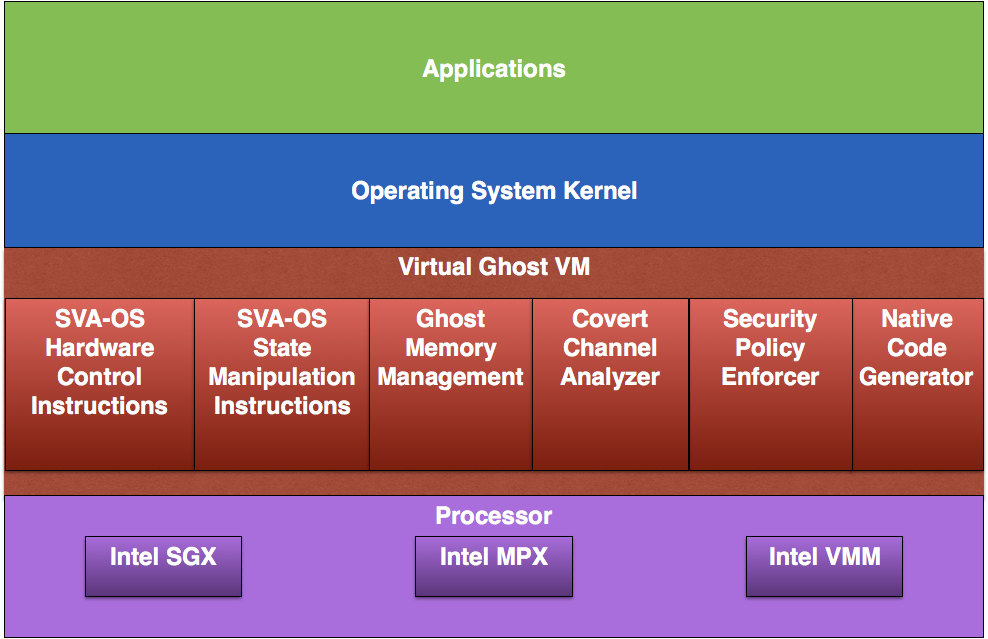
Virtual Ghost is a system which protects applications from a
compromised operating system kernel. While Virtual Ghost has
outperformed its predecessors, we want to make it even faster to make
it practical for use in environments with tight resource constraints
(such as mobile devices, large-scale data centers, and
cloud computing systems).
In the Apparition project, a collaboration with
Alan Cox at Rice University and Sandhya Dwarkadas
(now at the University of Virginia),
we extended Virtual Ghost to mitigate
side-channel attacks, namely some of the side-channel attacks that can
be launched by compromised operating system kernels and Spectre attacks.
Papers
Many programs have the ability to override an operating system's default
access control rules. Such programs are given attributes called
privileges which enable them to bypass these access control rules.
Operating systems such as Linux provide features that allow a running
program to enable and disable a subset of its privileges when needed and
to permanently disable privileges that are no longer required.
We have developed the PrivAnalyzer compiler which helps reduce the
privilege use of programs and helps programmers determine which types of
privilege use will lead to more secure programs.
Papers
