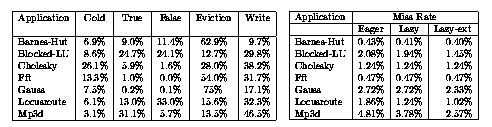
Table 2: Classification of misses and miss rates
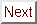
As mentioned in section 2, the main benefits of the lazy protocols stem from reductions in false sharing, and elimination of write buffer stall time when data is already cached read-only. In an attempt to identify the extent to which these benefits might be realized in our application programs, we have run a set of simulations to classify their misses under eager release consistency. Applications that have a high percentage of false sharing, or that frequently write miss on read-only blocks will provide the best candidates for performance improvements under lazy consistency.

Table 2: Classification of misses and miss rates
Table 2 presents the classification of the eager protocol's miss rate into the following components: Cold misses, True-sharing misses, False-sharing misses, Eviction misses, and Write misses. The individual categories are presented as percentages of the total number of misses. The classification scheme used is described in detail in [3]. Write misses are of a slightly different flavor from the other categories: they do not result in data transfers, since they occur when a block is already present in the cache but the processor does not have permission to write it. As can be seen from the table, the applications with a significant false miss rate component --- the ones that we would expect to see performance improvements for the lazy protocol --- are barnes-hut, blocked-lu, locus-route, and mp3d. The remaining applications (cholesky, fft, and gauss) should realize no gains in the lazy protocol since they have almost no false sharing. We have decided to evaluate them to examine whether the lazy protocol is detrimental to performance for applications without false sharing.